WikiLeaks on Thursday announced that it had released more Vault 7 documentation online, including details about several CIA projects to infect Apple's Mac computer firmware and operating system. The site of stolen Vault 7 data earlier this month. The CIA's Embedded Development Branch developed malware that could persist even if the targeted computer were reformatted and its OS were reinstalled, according to data WikiLeaks exposed.
The newly released files shone a spotlight on the CIA's efforts to gain 'persistence' in Apple devices, including Mac computers and iPhones, via malware designed to attack their firmware. One of the documents highlighted in Thursday's data dump exposes the 'Sonic Screwdriver' project, which likely was named for the handheld tool wielded by the science fiction character 'Doctor Who,' as the device seemingly can bypass any digital or mechanical lock. The CIA described it as a 'mechanism for executing code on peripheral devices while a Mac laptop or desktop is booting,' accordingly to WikiLeaks, to allow the attacker to gain access even if a firmware password were enabled. Who Is Listening The CIA has been infecting the iPhone supply chain of specific targets since at least 2008, a year after the release of the first iPhone, WikiLeaks claimed. It also released the CIA's manual for 'NightSkies 1.2,' described as a 'beacon/loader/implant tool' designed for use in infecting iPhones. 'Today's release appears to confirm that the CIA had developed tools to hack the iPhone well before most people ever owned one,' warned Ed McAndrew, cybersecurity partner at and former cybercrimes prosecutor with the U.S.
Attorney's Offices for the Eastern District of Virginia and for the District of Delaware. 'Infection within the supply chain illustrates how committed the agency was to widespread and persistent exploitation of these devices over the long term,' McAndrew told TechNewsWorld. 'With malware development moving at light speed, it is frightening to think of how the CIA's hacking capabilities have likely advanced from back then to today,' he added. 'Unfortunately, this release may provide little that will be useful to Apple or its development partners in eliminating vulnerabilities in today's devices.' Controlling the Firmware Also among the data released on Thursday is information on 'DarkSeaSkies,' a project that could implant UEFI (User Extensible Firmware Interface) - a specification that defines a software interface between an operating system and platform firmware - on an Apple MacBook Air computer. EFI/UEFI, which is expected to replace BIOS as the connection between firmware and a system's OS, typically is installed at the time of manufacturing and is the first program that runs when a computer is turned on. Controlling the UEFI would make it virtually impossible for anyone to remove the installed malware.
'If you want persistent access - which is an exploit that will remain available to you even after a user updates her software - then there is almost nothing better than control of the firmware,' said Jim Purtilo, associate professor in the computer science department at the. 'This gives you control of the device even before the user's software starts to run on it, and your defensive measures will guard digital premises that have already been violated,' he told TechNewsWorld. Bridge Between Hardware and Software The boot process reflects the increased complexity of modern devices - that is, how many bridges between hardware and software must be erected when a device is powered up.
Wikileaks Exposes Cia Infections For Macbeth
'It starts when a modest amount of hardware is used to load and execute commands which are stored in a special type of memory reserved just for this process, and these in turn will cause yet more commands to be loaded from the device's storage - perhaps a flash drive,' explained Purtilo. 'This is where it gets really complex, because there is so much variety in hardware anymore that one boot program can't do all the work itself. It must interrogate each subsystem to ask what special bridges or connections must be initialized for that component to work correctly too,' he added. 'Otherwise you risk that a display might come up with the wrong settings, or the phone would not be ready to connect to the local service.' Taking Command of a Computer Through the use of a special UEFI, a computer in essence can be monitored, modified or otherwise controlled by a third-party, often without the actual owner becoming aware of any loss of control. This could give the CIA untold power to monitor almost anyone. 'This boot process is an ideal place for an intruder to introduce his own commands,' said Purtilo.
'The hardware must necessarily trust the commands it is given at this point, and that's why designers do whatever we can to protect them from being corrupted by others,' he pointed out. The complexity of the device means there are many paths in - and to ensure integrity, it's necessary to guard all of them. 'What Wikileaks tells us is that the CIA found a path that the designers missed,' said Purtilo. 'The suggestion that you can exploit this defect with only quick access to 'factory fresh' phones - which is what they asserted - means the vulnerability is pretty fundamental, and that in turn tells us that the number of devices exposed by it could be huge.'
Infected Supply Chain WikiLeaks' Thursday release also includes documents suggesting that the CIA has developed the means to infect an organization's supply chain by interdicting mail orders and other shipments. Tactics could include opening boxes and infecting the machines, and then resending them to their destinations. That suggests even brand new machines could be infected before they come out of the box. 'The significance of these disclosures is not so much the specifics of the tools used, but that the CIA was able to access new-in-the-box devices through a known vector of vulnerability,' said Robert Cattanach, partner at. 'Similar exploits in the future cannot be ruled out, and the effectiveness of ongoing protections is limited by the imagination of those attempting to anticipate potential vulnerabilities,' he told TechNewsWorld. The bottom line is that 'the more sensitive the information, the less willing one should be to trust the security of any device,' Cattanach added.
The Intelligence Game It's questionable whether the information leaked should be considered very revealing, given the way intelligence operates today. The mission of U.S. Intelligence services is to 'gather intelligence against those with the intention and capability to harm our national security,' explained Cattanach. 'Those agencies presumably will attempt to access information in any way technically possible, using methods that are as difficult to protect as possible,' he added. 'Legal nuances are will likely be skirted, and potentially ignored outright.' It's unlikely that Apple is the only company that should consider its products vulnerable to malware and spying by the CIA and other intelligence agencies. 'Until we know more specifics, I would not presume that this is limited to only Apple products,' said Purtilo.
'The hardware instructions would be tailored to a given platform, of course, but depending on what flaw is being exploited, the approach might be similarly applied to other systems in the same chipset family.' Peter Suciu has been an ECT News Network reporter since 2012. His areas of focus include cybersecurity, mobile phones, displays, streaming media, pay TV and autonomous vehicles. He has written and edited for numerous publications and websites, including Newsweek, Wired and FoxNews.com.
Share this story. Home routers from 10 manufacturers, including Linksys, DLink, and Belkin, can be turned into covert listening posts that allow the Central Intelligence Agency to monitor and manipulate incoming and outgoing traffic and infect connected devices. That's according to secret documents posted Thursday by WikiLeaks., as the implant is code-named, can be especially effective against targets using some D-Link-made DIR-130 and Linksys-manufactured WRT300N models because they can be. An can extract their passwords as long as a default feature known as universal plug and play remains on.
Routers that are protected by a default or easily-guessed administrative password are, of course, trivial to infect. In all, documents say CherryBlossom runs on 25 router models, although it's likely modifications would allow the implant to run on at least 100 more.
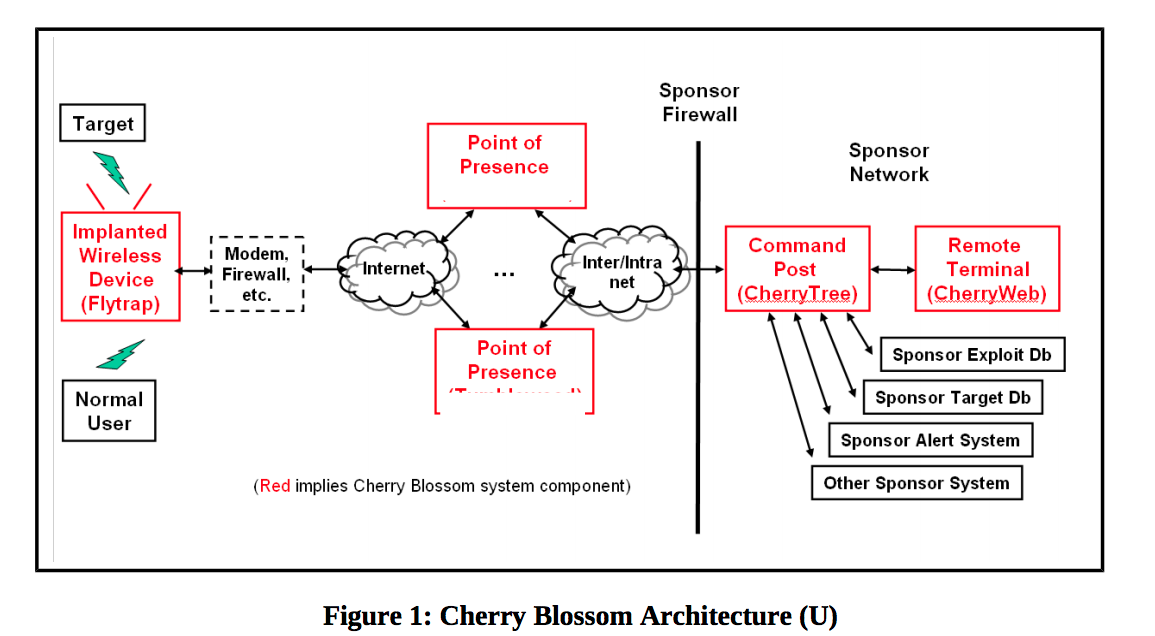
WikiLeaks The describes a Linux-based operating system that can run on a broad range of routers. Once installed, CherryBlossom turns the device into a 'FlyTrap' that beacons a CIA-controlled server known as a 'CherryTree.' The beacon includes device status and security information that the CherryTree logs to a database. In response, the CherryTree sends the infected device a 'Mission' consisting of specific tasks tailored to the target. CIA operators can use a 'CherryWeb' browser-based user interface to view Flytrap status and security information, plan new missions, view mission-related data, and perform system administration tasks. Missions can target connected users based on IPs, e-mail addresses, MAC addresses, chat user names, and VoIP numbers. Mission tasks can include copying all or only some of the traffic; copying e-mail addresses, chat user names, and VoIP numbers; invoking a feature known as 'Windex,' which redirects a user's browser that attempts to perform a drive-by malware attack; establishing a virtual private network connection that gives access to the local area network; and the proxying of all network connections.
Further ReadingIn many respects, CherryBlossom isn't much different from and other types of that have infected hundreds of thousands of devices over the past few years. What sets the CIA implant apart the most is its full suite of features, including its user interface, command-server support, and a long list of mission tasks. Also significant: the documents date back to 2007, when router hacking was less developed than it is now. CherryBlossom is the latest release in WikiLeaks Vault7 series, which the site purports was made possible when the 'CIA lost control of the majority of its hacking arsenal.' CIA officials have declined to confirm or deny the authenticity of the documents, but based on the number of pages and unique details exposed in the series, there is broad consensus among researchers that the documents are actual CIA materials.
What's more, researchers from security firm Symantec have that has been penetrating governments and private industries around the world for years. While WikiLeaks said Vault7 was intended to 'initiate a public debate about the security, creation, use, proliferation, and democratic control of cyberweapons,' little or nothing published to date has shown the CIA running afoul of its legal mandate. Further ReadingLike the other Vault7 releases, Thursday's installment doesn't include the source code or binaries that would allow other hacker groups to appropriate the CIA's router-hijacking capabilities. That makes the leaks significantly less damaging than those by the Shadow Brokers, the name used by a still-unknown group that has been published advanced hacking tools developed by and later stolen from the National Security Agency. April's resulted in the that infected an. Thursday's Vault7 release does, however, provide so-called indicators of compromise that targets can use to determine if they were hacked. As pointed out by a researcher who tweets under the handle Xorz, it may allow people to identify CIA-controlled CherryTree servers, since they all seem to.
A general defense more technically inclined users can take against router-based malware that monitors and tampers with Internet traffic is to put the router in question into passive mode and connect it to network hub and a trusted router. This allows the person to see all traffic going into and out of the network. Promoted Comments.
Wikileaks Exposes Cia Infections For Mac
So, presumably, those of us running custom router firmware (tomato, dd-wrt) don't need to worry? Or should I turn UPNP off anyway?
You should always disable UPnP on any router, IMO, unless you have a very good reason not to do so. Generally speaking, anything that allows a device to automatically adjust settings is a horrible security vulnerability waiting to happen. With how critical a router is to overall security of a network, it's a no-brainer to kill as much as possible.

The only reason to have UPnP at all is so novices can use advanced features such as routing external traffic to a specific device without the need to tinker in the settings. If you're capable of installing custom firmware on the device, you're more than capable to set those things up yourself.
The CIA's focus is external intelligence. The 4th Amendment does not apply beyond the borders of the US.
Barring it being a US citizen or national, of course, and I don't believe anyone has shown they routinely target those. Not that the surveillance state is an entirely positive thing, mind you. I think we need much better controls on the various agencies. That does not, however, justify knee jerk reactions which aren't even accurate.
All that sort of lazy argument does is give those who disagree an easy out. 'cause they do it I can do it' is fucked up. It may be pragmatic but it is fucked. 'Virginia has slaves, Kentucky must have slaves too'. I mean, it is pragmatic.
Sometimes I think of Ars as a Moot and I'm cool with that but at least leave obtuse in the grass. It's not a matter of 'cause they do it I can do it'. Rather it's 'cause they do it I have to do it'. We don't have much to fear from the UK, Canada, Australia and New Zealand. We have a lot to fear from Russia, North Korea, and various other counties. If we don't engage in these activities then we will be at a disadvantage because those countries will continue.

We've been lucky that the Five Eyes are willing to work together both politically and economically. The rest of the world is not so accommodating.